Table of Contents
- 1. Call authentication reduces spam losses
- 2. Introduction to STIR/SHAKEN
- 3. Definition of STIR and SHAKEN
- 4. How STIR/SHAKEN works
- 5. Importance of call authentication
- 6. Economic impact of spam calls
- 7. Benefits of STIR/SHAKEN compliance
- 8. Requirements for implementing STIR/SHAKEN
Call authentication reduces spam losses
- Caller ID authentication seeks to curb spoofing and robocalls, two drivers of phone spam.
- Businesses lost $39 billion to spam calls in 2023 (CFCA).
- STIR/SHAKEN adds cryptographic verification to VoIP/SIP calls to distinguish legitimate calls from fraud attempts.
- In the U.S., compliance is tied to regulatory requirements (FCC) and the possibility that unverified calls may be blocked or labeled.
Introduction to STIR/SHAKEN
For any business that relies on the phone—contact centers, sales teams, support, or collections—the problem is no longer just “making calls,” but getting them delivered and answered. In an environment saturated by billions of unwanted calls, caller ID has ceased to be a reliable signal: many numbers “look real,” but a significant share are spoofed.
In that context, STIR/SHAKEN emerges, a technical and policy framework driven by authorities and phone networks to verify numbers before the recipient’s phone rings. The idea is simple in its goal, complex in its execution: if a call can cryptographically prove that the originator is authorized to use the number it presents, the terminating network can treat it as trustworthy; if it cannot, it can label it as possible spam or outright reject it.
The framework is especially rooted in the VoIP world, where traffic travels over SIP (Session Initiation Protocol) and where Caller ID spoofing has historically been easier to scale. STIR/SHAKEN does not “eliminate” phone fraud by itself, but it introduces an authentication layer that shifts the balance: it makes it harder for an attacker to hide behind fake numbers and makes it easier for operators to apply controls.
In addition, STIR/SHAKEN is not just a technical recommendation. In the United States, the FCC has established obligations and certification and reporting mechanisms (including a robocall mitigation database) that make compliance an operational requirement for many players in the ecosystem, including VoIP providers and resellers.
Definition of STIR and SHAKEN
STIR/SHAKEN is not a single standard, but the combination of two complementary pieces: STIR (the identity signing/verification technology in SIP) and SHAKEN (the handling, policy, and traceability framework that operationalizes that verification in voice networks). In practical terms, STIR provides the “cómo signs” and SHAKEN provides the “how that signature is used” to make call delivery decisions.
The combination makes it possible that, as a call traverses providers (origination, transit, termination), there is a consistent way to attach cryptographic evidence about the Caller ID and to interpret it at the receiving end. This is key because telephone fraud relies on asymmetry: it is cheap to spoof and expensive to investigate. STIR/SHAKEN tries to reduce that asymmetry with automation and verifiable trust.
In practice, when a company makes outbound calls using U.S. numbers (something common in call centers and VoIP resellers), compliance with STIR/SHAKEN becomes a factor that influences deliverability: calls without verification or with weak verification may be treated with greater suspicion by the terminating carrier.
Meaning of STIR
STIR stands for Secure Telephone Identity Revisited. It was established by the Internet Engineering Task Force (IETF) and defines a signing mechanism to confirm the calling number and the method of transmission within SIP.
Its central goal is to add a digital certificate to the SIP data that VoIP systems use to originate and receive calls. In other words: STIR introduces a standardized way to say “this number that appears as Caller ID is backed by a digital signature issued under a chain of trust.”
In a call flow, STIR materializes in the creation of a SIP Identity header (identity header) that contains information relevant to validating the call, such as the dialed number, a timestamp, the Caller ID associated with STIR/SHAKEN, the attestation level, and an origination identifier. That header travels with the call (or, if the network is not SIP, it can travel via an alternative out-of-band mechanism).
The importance of STIR is that it turns a historically “declarative” attribute (Caller ID) into a verifiable attribute. It does not prevent malicious calls from existing, but it does make it harder for them to present themselves as if they were from a legitimate third party without leaving a verifiable trace.
Meaning of SHAKEN
SHAKEN stands for Signature-based Handling of Asserted information using toKENs. Unlike STIR—more focused on the technical specification of the signature—SHAKEN integrates a trusted Caller ID authentication procedure with a more automated traceback capability to reduce the impact of illegal spoofing.
It also provides guidance for handling VoIP conversations that contain incorrect or missing STIR data. This is relevant because the real world nor is homogeneous: there are network segments, interconnections, and scenarios (for example, certain international flows) where information can degrade or be unavailable.
In operational terms, SHAKEN helps turn verification into decisions: what to do when the signature is valid, when it isn’t, when the chain of trust is broken, or when the call arrives without the necessary elements. That “policy layer” is what allows the terminating operator to label or block calls, and for the ecosystem to have a common language to talk about trust.
That’s why it’s often summarized like this: STIR is technology; SHAKEN is policy. Together, they make it possible to authenticate and manage telephone identity more robustly.
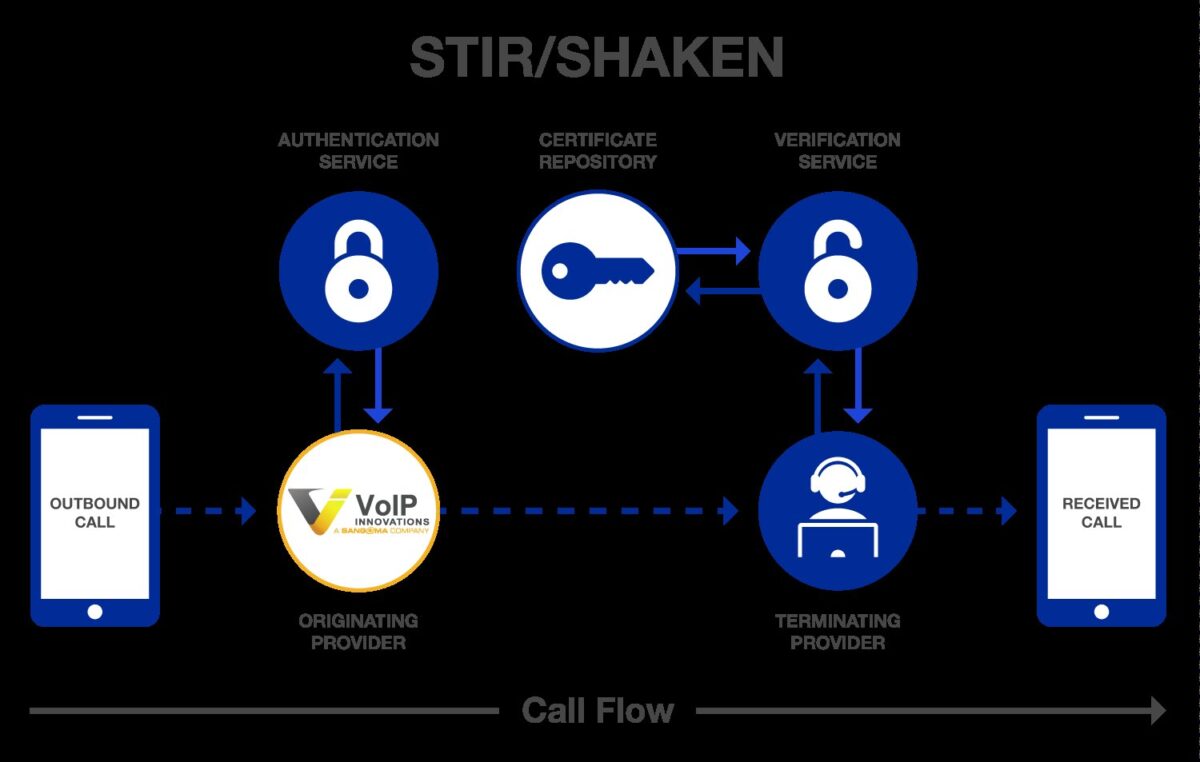
How STIR/SHAKEN works
How STIR/SHAKEN works is based on digital certificates and on verifications between service providers. The goal is that, before a call reaches the end user, the network can assess whether the Caller ID is authentic and with what degree of confidence.
In a call center or an enterprise environment, this translates into a critical point: number reputation and identity consistency. If outbound traffic cannot be properly signed or arrives with weak attestations, the destination operator may treat it as suspicious. By contrast, when the flow is well implemented, the call can arrive with a verified identifier, reducing the likelihood of being labeled as spam.
The process, as described in typical implementations, occurs in stages: call initiation, attestation assignment, signing, transmission, verification, and finally, delivery or corrective action (labeling/blocking). In non-SIP networks, there is the possibility of transporting the identity token separately via Out-of-Band SHAKEN.
The essential point is that verification does not depend on a single company: it is a network-to-network mechanism. That’s why coordination between providers (originating and terminating) and access to certificates within a chain of trust are structural pieces of the system.
Call authentication process
1) Call initiation: when a call is made, a SIP INVITE (request to initiate the call) is sent to the originating service provider. This is the first point where an attempt is made to establish the legitimacy of the originator.
2) Assignment of the attestation level: after verifying the caller’s details, the provider assigns one of the three levels of STIR/SHAKEN attestation. That level functions as a trust rating that will travel with the call.
3) Creation of digital signatures: a digital certificate is used to sign the identier identity and generate the SIP Identity header. This header includes elements such as the dialed number, timestamp, Caller ID associated with STIR/SHAKEN, attestation level, and origin identifier.
4) Transmission: the identity header and the call are transmitted to the terminating provider. If the call traverses non-SIP networks, the identity token can be sent separately via Out-of-Band SHAKEN when necessary.
5) Authentication and verification: the terminating provider obtains the caller’s digital certificate from an open source and verifies three points: that the header matches the SIP INVITE, that the digital signature is legitimate, and that the certificate trust chain is not broken.
6) Termination: if everything is correct, the call reaches the recipient with verified Caller ID. If verification fails, the call can be blocked or flagged as possible spam.
Attestation levels in STIR/SHAKEN
STIR/SHAKEN defines three attestation levels that the provider assigns to each call. In practice, they are a signal for the terminating provider to decide whether it allows, blocks, or treats the traffic with caution.
-
Level A (Full Attestation): the provider fully knows the customer’s identity and verifies that they are authorized to use the number they present. This is the highest-trust scenario.
-
Level B (Partial Attestation): the provider verifies the end user, but cannot verify the origin of the phone number. The customer’s identity is validated, but the relationship to the number is not fully supported.
-
Level C (Gateway Attestation): the provider is only forwarding the call; it cannot confirm the originator’s identity or determine whether they are authorized to use the number. This is common in situations involving international numbers.
In international calls an additional challenge appears: the North American Numbering Plan (NANP) requires international originators to provide domestic gateway providers with information and tools to confirm identity. Even so, from the perspective of trust and deliverability, working with carriers capable of providing full authentication is presented as the ideal option if the goal is for calls to be trustworthy and answered.
Importance of call authentication
Call authentication has become a component of security and operational continuity. Caller ID spoofing doesn’t just annoy users: it allows scammers to impersonate banks, orgpublic bodies or well-known brands, and that erodes overall trust in the phone channel. When the user stops believing in the caller ID, the damage spreads to legitimate businesses: more ignored calls, more friction in sales and support, and a greater risk that corporate numbers end up being blocked.
STIR/SHAKEN addresses that problem with one principle: verify before delivering. If the terminating operator can confirm that the presented number is signed and that the signature comes from a trusted chain, the call can be treated as legitimate. If not, the network has grounds to warn about or curb the traffic. This is especially relevant in VoIP, where volume and ease of automation have fueled the growth of robocalls.
Authentication also helps differentiate between legitimate automation and fraud. The ecosystem itself recognizes that there are valid robocalls (for example, prerecorded payment reminders), but the problem is when they are used to deceive. With identity verification, the recipient has more tools—and the network more criteria—to separate the authentic from the fake.
In addition, authentication ties into regulatory compliance. In the U.S., the FCC has required measures against robocalls and has strengthened carriers’ ability to reject fraudulent calls and texts originating from non-compliant networks. In that framework, authentication is not an “extra”: it is part of the language the network uses to decide which traffic deserves trust.
Economic impact of spam calls
Phone spam is not an abstract cost: it translates directly into losses, fraud, and deterioration of commercial effectiveness. One figure illustrates the magnitude: according to CFCA, businesses lost $39 billion to spam calls in 2023. That number reflects the aggregate impact of scams, spoofing, and illicit operations that rely on the voice channel.
Volume also matters because it saturates the system and changes user behavior. In the United States, it was reported that in December 2023 Americans received more than 3 billion robocalls, equivalent to nearly 17 spam calls per person. When users live under that pressure, their rational response is to distrust: not answering unknown numbers, hanging up faster, or relying on automatic “possible spam” labels. That distrust, while it protects consumers, hits companies that call for legitimate reasons.
The problem is not limited to one country. Estimates are cited that robocalls accounted for 25% of all incoming calls to Canadian numbers in 2021, and coordination by the U.S. FTC with Canada in enforcement actions is mentioned. The pattern is consistent: fraud crosses borders, and thecost is shared among consumers, carriers, and brands.
In that scenario, STIR/SHAKEN is presented as a response that seeks to reduce the economic cost in two ways: decreasing the ability to spoof (and therefore fraud) and improving the deliverability of legitimate calls, preventing commercial operations from losing revenue due to blocked or ignored calls.
Benefits of STIR/SHAKEN compliance
Compliance with STIR/SHAKEN has become a practical lever to restore trust in the voice channel. Its promise is not “to make spam disappear,” but to better distinguish between real and fake calls, and allow the network to act accordingly. For businesses, that translates into operational benefits: more completed calls, less risk of numbers being labeled as spam, and a stronger foundation for meeting regulatory requirements.
The framework also helps reduce reputational damage. When scammers use fake numbers to impersonate a brand, the consumer does not always distinguish the impostor from the original: they associate the negative experience with the name they thought they saw. Authentication reduces that attack surface by making it harder for a third party to present a “borrowed” Caller ID without verifiable backing.
Another benefit is user time efficiency. If the recipient can better distinguish between legitimate calls and spam, they devote more attention to real communications. Taken together, this improves the quality of the phone channel as a tool for service, sales, and support.
Finally, there is the compliance component: the FCC has required STIR/SHAKEN for voice providers and has strengthened the authority to reject fraudulent traffic from non-compliant networks. For companies that rely on VoIP providers or that resell services, compliance stops being a technical issue and becomes a requirement to sustain operations without interruptions.
Increased answer rates
One of the most direct benefits is an increased likelihood that a call will be answered. The logic is behavioral: when the customer perceives that the Caller ID is authentic, suspicion decreases and willingness to answer increases. For sales teams and outbound contact centers, that difference is critical: an unanswered call is not only a failed attempt, it is also wasted time and operating cost.
STIR/SHAKEN contributes to that outcome by allowing the call to arrive with a verified identifier. If the terminating carrier validates the signature and the chain of trust, the call can be completed without being marked as “possible spam.” In an environment where users receive massive volumes of robocalls, that signal of authenticity becomes a decision factor.
The benefit is amplified when the eThe company maintains consistency: stable numbers, properly signed traffic, and stronger attestations. Although STIR/SHAKEN does not by itself guarantee that the user will answer, it does reduce a key barrier: doubt about whether the number is spoofed.
In business terms, more answers imply more real conversations: more sales opportunities, more effective support contacts, and less need to repeat attempts. In a channel where trust has eroded, verification becomes a way to rebuild it with technical evidence.
Reduction of unwanted calls
STIR/SHAKEN is also aimed at reducing the impact of spam and robocalls by making them easier to identify and block. By using digital certificates and verification between providers, the system allows the terminating operator to detect calls with invalid signatures, inconsistent data, or broken chains of trust, and then block or label them as suspicious.
This is relevant because many frauds rely on spoofing: presenting a number that does not belong to the attacker to gain credibility. With authentication, that tactic loses effectiveness when the number cannot be backed by a valid signature. The framework is mentioned as useful for reducing several types of scams:
- Robocalls: although some are legitimate (for example, payment reminders), many are fraudulent. STIR/SHAKEN can help illegitimate attempts be labeled or blocked.
- Vishing (voice phishing): calls that seek to extract financial or personal information. Caller ID verification makes it easier to recognize fake calls.
- Phishing: impersonation of banks, public agencies, or card issuers to obtain sensitive data.
- Tech support scams: impostors who claim to detect problems and push users to install malware.
For companies, reducing unwanted calls has a double effect: it protects customers (less exposure to fraud associated with their brand) and improves the voice ecosystem, making legitimate calls compete less with the noise of spam.
Requirements for implementing STIR/SHAKEN
Implementing STIR/SHAKEN is not limited to installing a technical feature: it involves meeting registration, certification, and reporting requirements, especially in the United States under the FCC framework. To participate, providers must be identified and validated within a trust system that enables the issuance and use of certificates.
Among the requirements mentioned for telephone service providers are:
- Have an up-to-date Form 499-A filed with the FCC.
- Have an Operating Company Number (OCN) valid.
- Register in the FCC Robocall Mitigation Database (RMDB) to certify actions taken to implement STIR/SHAKEN and prevent robocalls.
In addition, to participate in the STIR/SHAKEN service, the following is required:
- Registration with the Policy Administrator (STI-PA), which authenticates the carrier.
- Selection of an authorized Certification Authority (STI-CA), which verifies that certificate applicants are qualified and that the STI-PA validated their credentials.
- Obtain an SPC TOKEN from the STI-PA, which enables providers to request a certificate.
- Request a certificate from an authorized STI-CA, necessary to digitally sign and authenticate calls.
A relevant regulatory change was set with new FCC rules that take effect on June 20, 2025: providers subject to an implementation obligation should no longer rely on an upstream to sign calls on their behalf. For VoIP resellers in the U.S. under requirements, this implies obtaining their own certificate and integrating the protocol into their infrastructure, in addition to updating their mitigation plan in the RMDB indicating their implementation status (full, partial, or none) and the reason.
Challenges in the adoption of STIR/SHAKEN
Adopting STIR/SHAKEN is, for many players, a race of technical integration, coordination among providers, and regulatory compliance. One of the most cited challenges is that not everyone starts from the same point: small providers and VoIP resellers may face barriers to incorporating call signing, managing certificates, and upgrading infrastructure.
Cost and operational complexity also weigh in. Implementing signing with certificates, maintaining the chain of trust, and sustaining compliance processes (registrations, mitigation plan updates) adds burden. In particular, the regulatory change that takes effect on June 20, 2025 raises the bar for certain providers: those who were relying on an upstream to sign calls must move to a model with their own certificate and direct integration.
Another challenge is coverage in international scenarios. The scheme itself recognizes that Level C (Gateway Attestation) is common with international numbers, where the provider delivering the call cannot confirm identity or authorization to use the number. Although the NANP requires international originators to provide information and tools to domestic gateways to confirm identity, the reality of interconnections and transits can degrade the quality of attestation. This limits the system’s effectiveness in certain global flows.
Finally, there is a challenge
de perception: even with verified calls, if the consumer does not understand what that verification means or remains conditioned by years of spam, they may remain cautious. Technology improves the trust signal, but user behavior adjusts more slowly, especially when the volume of robocalls has been so high.
Conclusions on STIR/SHAKEN compliance
STIR/SHAKEN has established itself as a structural response to the deterioration of the phone channel caused by robocalls and Caller ID spoofing. Its core value is turning telephone identity into something verifiable through digital certificates and a chain of trust between providers, allowing the network to decide more soundly which calls to deliver, which to label, and which to block.
The available data show why the issue is urgent: business losses of $39 billion in 2023 due to spam calls (CFCA) and volumes such as more than 3 billion robocalls in the U.S. in December 2023. In that context, compliance is not just a matter of “security”: it is a factor that affects deliverability, reputation, and commercial effectiveness.
In the United States, moreover, the regulatory component is decisive. The FCC has required measures and has strengthened carriers’ ability to reject fraudulent traffic from non-compliant networks. The rules that take effect on June 20, 2025 underscore the direction: greater direct responsibility for providers (including VoIP resellers) to sign calls and accurately report their status in the RMDB.
The practical conclusion for businesses and contact centers is clear: if they rely on U.S. numbers and VoIP to operate, STIR/SHAKEN compliance becomes a condition for sustaining customer trust and reducing the risk that their calls end up being treated as spam.
Importance of STIR/SHAKEN Compliance
Benefits of Implementing STIR/SHAKEN
Implementing STIR/SHAKEN strengthens trust in caller ID by backing it with cryptographic verification. In practice, this helps legitimate calls get through more often without being flagged as suspicious, and reduces the room for scammers to spoof numbers associated with real brands. It also helps users better distinguish between lawful calls and spam, reserving their attention for authentic communications.
From an ecosystem standpoint, the benefit is systemic: by standardizing how calls are signed and how that signature is interpreted, it becomes easier for operators to apply consistent controls against robocalls and spoofing. For businesses that call clienyou, the desired outcome is less friction: more completed calls, fewer blocks, and less reputational damage from spoofing.
Challenges in the Adoption of STIR/SHAKEN
Adoption faces technical and coordination challenges: integrating call signing, managing certificates, and ensuring that information travels correctly across heterogeneous networks. In international scenarios, attestation can degrade to lower-trust levels (such as level C), because the gateway provider cannot always verify the identity and authorization of the number.
Added to this is regulatory compliance: filings, certifications, and updates to mitigation plans. The regulatory change effective June 20, 2025 adds pressure on VoIP providers and resellers that previously relied on third parties to sign calls, forcing them to assume that capability directly.
Steps to Ensure Compliance
Within the framework described for the U.S., ensuring compliance involves completing formal and technical requirements. Key steps include: keeping information up to date with the FCC (such as Form 499-A), having a valid OCN, registering and certifying actions in the Robocall Mitigation Database (RMDB), and participating in the certificate ecosystem through STI-PA and an authorized STI-CA.
Operationally, it also involves obtaining the SPC TOKEN, requesting the corresponding certificate, and using it to sign calls. For VoIP resellers subject to the obligation, the recent regulatory emphasis is explicit: have their own certificate and integrate STIR/SHAKEN into their infrastructure, in addition to declaring in the RMDB whether implementation is full, partial, or nonexistent and why.
The Future of STIR/SHAKEN in the Business Environment
The framework points to an evolution in which the network has greater ability to reject fraudulent traffic and in which telephone identity is less “declarative” and more verifiable. Since spam and spoofing do not disappear on their own, the regulatory and operational trend suggests progressive tightening: more requirements for direct signing, more transparency in mitigation plans, and more authority to block traffic from noncompliant networks.
For the business environment, the immediate future hinges on deliverability: as operators place more trust in authentication signals, calls without verification or with weak attestations will tend to face more friction (labeling, blocking, or a lower response rate). In parallel, the pressure to properly manage complex scenarios—such as international traffic—will remain a critical point.
The Importance of STIR/SHAKEN Compliance for Telecommunications Companies
Introduction to STIR/SHAKEN
For telecommunications companies and VoIP providers, STIR/SHAKEN is both a technical standard and an interconnected trust framework. It relies on SIP, digital certificates, and inter-carrier verification to authenticate Caller ID, with the goal of reducing robocalls and spoofing. In the U.S., it also ties into FCC obligations and mechanisms such as the RMDB, which require declaring actions and implementation status.
Benefits of STIR/SHAKEN Compliance
Compliance makes it possible to sign calls and provide verifiable evidence of the caller’s identity. This enables terminating carriers to complete calls with greater confidence and to block or label suspicious traffic. As a result, the impact of fraud is reduced, brand reputations are protected, and the user experience is improved by making it easier to distinguish between legitimate calls and spam.
There is also an operational continuity benefit: in an environment where the FCC strengthens the ability to reject traffic from non-compliant networks, staying current with requirements and certifications reduces the risk of outages, degraded deliverability, or regulatory conflicts.
Challenges in Implementing STIR/SHAKEN
Implementation involves managing certificates, SIP integrations, and verification processes in an ecosystem with multiple interconnections. International scenarios often push toward weaker attestations (gateway), which limits the trust that can be assigned to certain calls. In addition, regulatory changes—such as the rule effective on June 20, 2025 that discourages relying on upstream providers for signing—force some players to redesign their architecture and responsibilities.
Steps to Achieve Compliance
The steps described include: meeting FCC requirements (updated 499-A, valid OCN), registering and maintaining a plan in the Robocall Mitigation Database, registering with STI-PA, choosing an STI-CA, obtaining an SPC TOKEN, and requesting the certificate to sign calls. For VoIP resellers subject to the obligation, the requirement to have their own certificate and integrate STIR/SHAKEN is added, along with updating the mitigation plan before June 20, 2025 indicating the level of implementation.
Conclusion
Compliance with STIR/SHAKEN has become a practical requirement to sustain trust in the voice channel: it reduces the margin for spoofing, helps curb robocalls, and improves the proba
bility for legitimate calls to be delivered and answered. With business losses quantified in the tens of billions and regulators strengthening the ability to block non-compliant networks, the message to the sector is unequivocal: call authentication is no longer optional in markets where it applies, and its correct implementation conditions both compliance and commercial effectiveness.
The importance of STIR/SHAKEN compliance becomes even more critical when voice is an operational channel that must reach, be verified, and be resolved without friction. From Suricata Cx’s perspective, strengthening call authentication and traceability helps protect the operator’s reputation and sustain a reliable omnichannel experience, where automation and human control work with stronger identity signals.
Sources and scope
This article is based on the dossier material, including Dialer360’s article on STIR/SHAKEN and cited regulatory references (FCC/RMDB), as well as figures attributed to CFCA and reports on robocall volume mentioned in the text. The content is informational and does not replace legal or compliance advice; applicable requirements may vary depending on the role (carrier, VoIP provider, or reseller) and the use case.
Editorial note
The approach is presented from an operational CX perspective for telecom and ISPs (Suricata Cx): how call authentication impacts deliverability, user trust, and continuity of the voice channel within omnichannel operations.

Martin Weidemann is a specialist in digital transformation, telecommunications, and customer experience, with more than 20 years leading technology projects in fintech, ISPs, and digital services across Latin America and the U.S. He has been a founder and advisor to startups, works actively with internet operators and technology companies, and writes from practical experience, not theory. At Suricata he shares clear analysis, real cases, and field learnings on how to scale operations, improve support, and make better technology decisions.